How to Save Windows 10’s Lock Screen Spotli
By default, Windows 10 shows background pictures on you...

Curiosity builds lifelong learning.
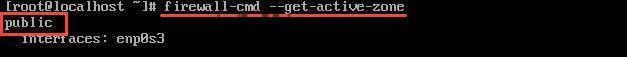
1. Start by checking your active firewalld zone:
firewall-cmd --get-active-zonesThe output will show your firewalld zone. In the example below, it is public.
2. Add the openvpn service to the list of services firewalld allows within the active zone. The active zone in our example is public. If your active zone is trusted, modify the command accordingly.
firewall-cmd --zone=public --add-service openvpn3. Next, make the settings above permanent by running the command:
firewall-cmd --zone=public --add-service openvpn --permanent4. To check whether the openvpn service was added use:
firewall-cmd --list-services --zone=public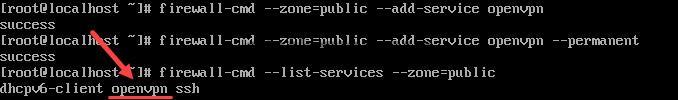
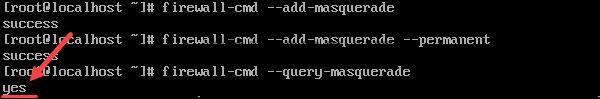
5. Then, add a masquerade to the runtime instance:
firewall-cmd --add-masquerade6. And make it permanent:
firewall-cmd --add-masquerade --permanent7. Verify the masquerade was added by running:
firewall-cmd --query-masqueradeThe output should respond with yes.
Once you have completed the steps above, move on to routing to your OpenVPN subnet.
1. Create a variable that represents the primary network interface used by your server. In the command below, the variable is named VAR. However, you can create a variable under the name of your choice.
VAR=$(ip route get 208.67.222.222 | awk 'NR==1 {print $(NF-2)}')2. Next, permanently add the routing rule using the variable created above:
firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.0.0/24 -o $VAR -j MASQUERADE3. Reload firewalld for the changes to take place:
firewall-cmd --reload4. Move on to routing all web traffic from the client to the server’s IP address by enabling IP forwarding. Open the sysctl.conf file:
vi /etc/sysctl.conf5. Add the following line at the top of the file:
net.ipv4.ip_forward = 16. Finally, restart the service:
systemctl restart network.service
iptables -t nat -I POSTROUTING -o eth0 \
-s 10.8.0.0/24 -j MASQUERADE
VAR=$(ip route get 208.67.222.222 | awk 'NR==1 {print $(NF-2)}')
firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.0.0/24 -o $VAR -j MASQUERADE
firewall-cmd --reload
/etc/rc.d/rc.local
sleep 1 echo "Cactus Software Solutions" sudo bash /root/enable_masquerade.sh
Source: phoenixnap